AAD connect Installation
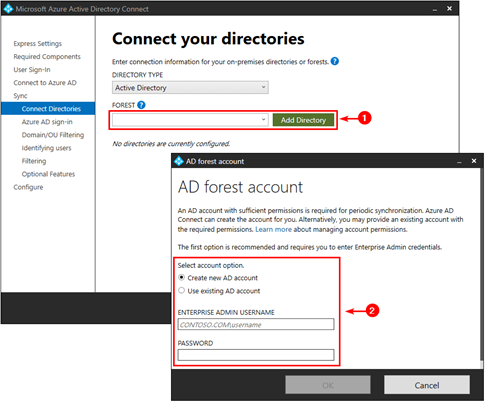
During the AD connect customize setup installation, you will see the below window to enter the Service account cred.
1: Create New AD account: This will ask you to enter Enterprise Admin credential to create new AD connector account like MSOL_cer44rwXXX
In AAD connect when you check Connector properties you will see MSOL account showing. But when you check in Services.msc for AAD connect you will see Enterprise Admin cred.
2: Use existing AD account: This option work only when you have created a Service account already with proper permission.
What type of permission required to be with Service account ?
|
Permission |
Used for |
|
Password hash sync |
|
Read/Write all properties User |
Import and Exchange hybrid |
|
Read/Write all properties iNetOrgPerson |
Import and Exchange hybrid |
|
Read/Write all properties Group |
Import and Exchange hybrid |
|
Read/Write all properties Contact |
Import and Exchange hybrid |
|
Reset password |
Preparation for enabling password write back |
Download the PowerShell Module or Import from the server where you have old version of AAD connect installed:
ADSyncConfig.psm1
PowerShell Module file location if you already have AAD connect installed:
C:\Program Files\Microsoft Azure Active Directory Connect\AdSyncConfig\AdSyncConfig.psm1
Open PowerShell as Administrator and Install Remote Server Administration Tools:
PS C:\> Install-WindowsFeature RSAT-AD-Tools
This will allow the PS commands to communicate with DC.
Import the PowerShell module AdSyncConfig.psm1 from the location where you have saved:
1: Copy the file path
Shift+right click on the file and copy as path
2: Open PowerShell:
PS C:\> Import-Module “C:\Program Files\Microsoft Azure Active Directory Connect\AdSyncConfig\AdSyncConfig.psm1”
You will get the prompt to click yes to install the module.
3: Copy the distuingedName or DN value of the service account created and edit the below PS and run it 1 by 1:
Set-ADSyncBasicReadPermissions -ADConnectorAccountDN “CN=AADC SVC1,CN=Users,DC=GoldenFive,DC=local”
Permissions for MS-DS-Consistency-Guid
Set-ADSyncMsDsConsistencyGuidPermissions -ADConnectorAccountDN “CN=AADC SVC1,CN=Users,DC= GoldenFive,DC=local”
Password Hash Synchronization
Set-ADSyncPasswordHashSyncPermissions -ADConnectorAccountDN “CN=AADC SVC1,CN=Users,DC= GoldenFive,DC=local”
Password write back
Set-ADSyncPasswordWritebackPermissions -ADConnectorAccountDN “CN=AADC SVC1,CN=Users,DC= GoldenFive,DC=local”
Group write back
Set-ADSyncUnifiedGroupWritebackPermissions -ADConnectorAccountDN “CN=AADC SVC1,CN=Users,DC= GoldenFive,DC=local”
Exchange Hybrid Deployment
Set-ADSyncExchangeHybridPermissions -ADConnectorAccountDN “CN=AADC SVC1,CN=Users,DC= GoldenFive,DC=local”
$credential = Get-Credential (You will see the credentials prompt, enter the user cred which have admin rights.)
Restriction on AD DS Connector Account
Set-ADSyncRestrictedPermissions -ADConnectorAccountDN ‘CN=AADC SVC1,CN=Users,DC= GoldenFive,DC=local’ -Credential $credential
NOW YOU CAN USE THE SERVICE ACCOUNT IN AAD CONNECT, AS IT HAVE PROPER DELEGATE PERMISSIONS ON DC.
!!! Thank You for giving your time to read my blog !!!
